ArgoCD Image Updater를 사용하기 위해서는 Kustomize/Helm Chart를 사용해야 합니다.
조정하다
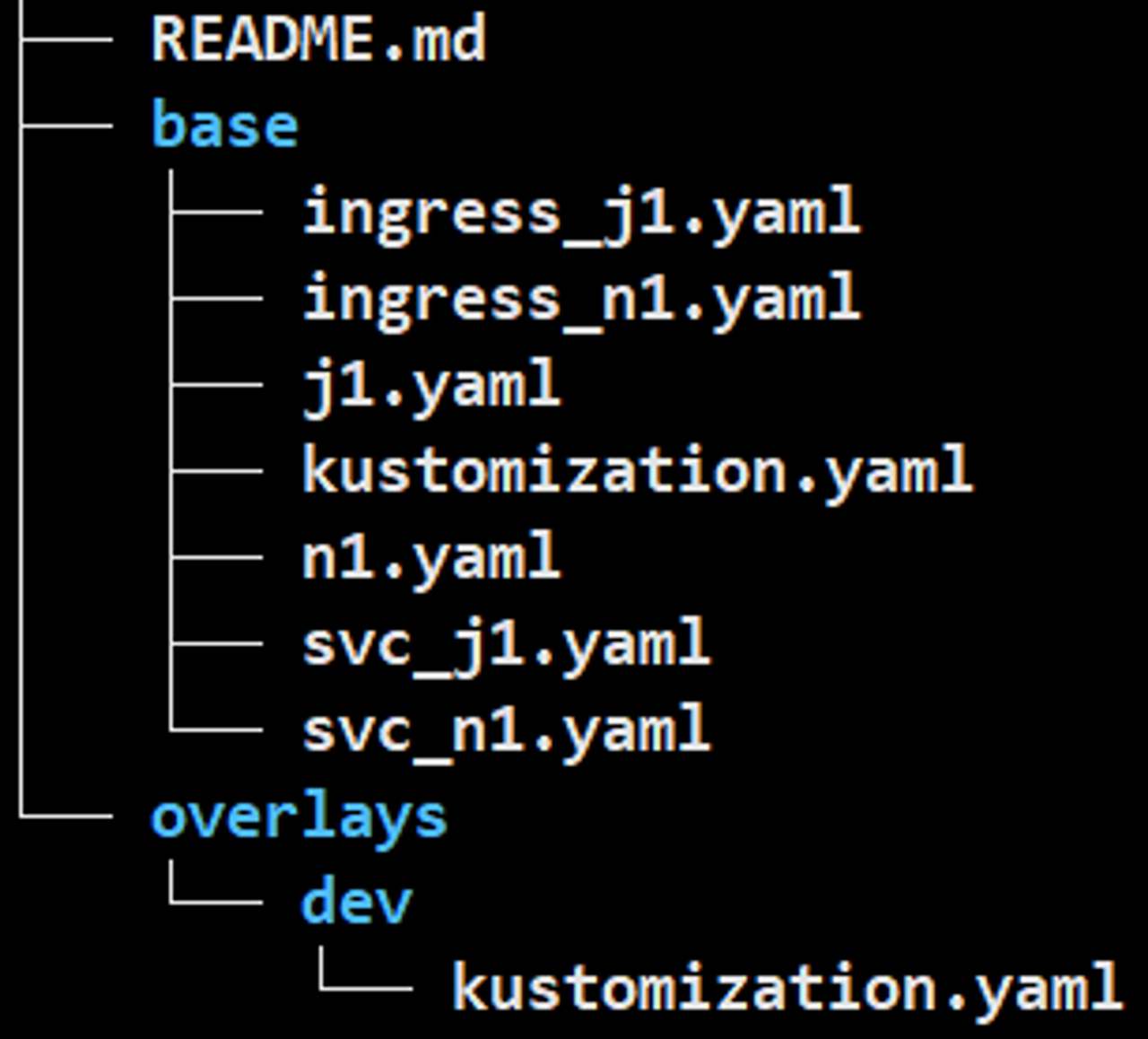
기본/kustomization.yaml
resources:
- n1.yaml
- j1.yaml
- ingress_n1.yaml
- ingress_j1.yaml
- svc_n1.yaml
- svc_j1.yaml
apiVersion: kustomize.config.k8s.io/v1beta1
kind: Kustomization
오버레이/dev/kustomization.yaml
apiVersion: kustomize.config.k8s.io/v1beta1
kind: Kustomization
images:
- name: <https://registry-1.docker.io/kangbock/nginx>
newTag: latest
- name: <https://registry-1.docker.io/kangbock/nodejs>
newTag: latest
resources:
- ../../base
cd overlays/dev/
kustomize edit set image <https://registry-1.docker.io/kangbock/nginx:latest>
cd ../..
kustomize build overlays/dev/.
ArgoCD 이미지 업데이터
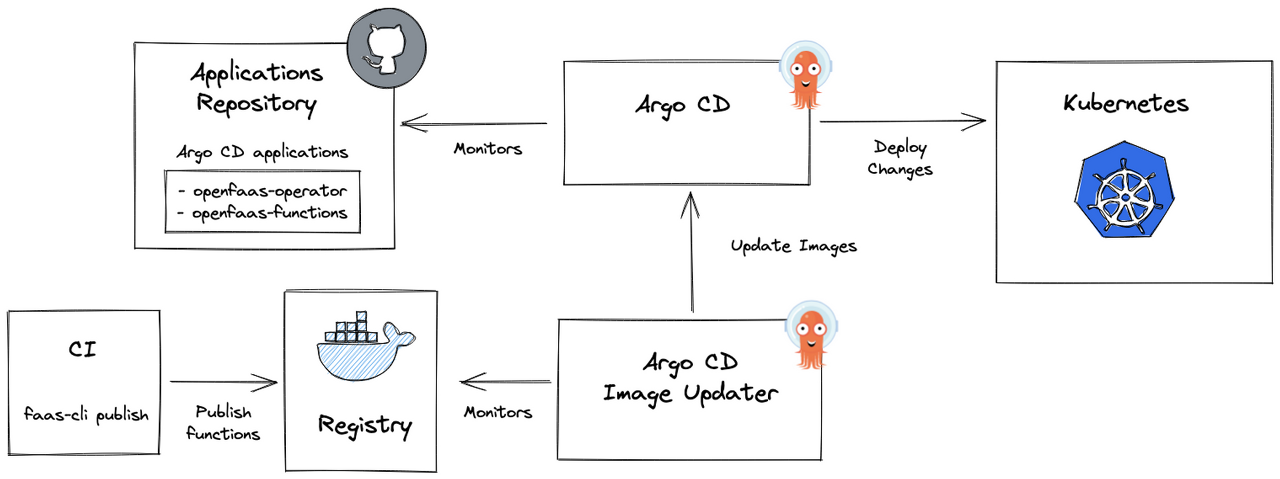
ArgoCD 이미지 업데이터
- ArgoCD 이미지 업데이터 install.yaml(참조)
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/name: argocd-image-updater
app.kubernetes.io/part-of: argocd-image-updater
name: argocd-image-updater
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/name: argocd-image-updater
app.kubernetes.io/part-of: argocd-image-updater
name: argocd-image-updater
rules:
- apiGroups:
- ""
resources:
- secrets
- configmaps
verbs:
- get
- list
- watch
- apiGroups:
- argoproj.io
resources:
- applications
verbs:
- get
- list
- update
- patch
- apiGroups:
- ""
resources:
- events
verbs:
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/name: argocd-image-updater
app.kubernetes.io/part-of: argocd-image-updater
name: argocd-image-updater
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: argocd-image-updater
subjects:
- kind: ServiceAccount
name: argocd-image-updater
---
apiVersion: v1
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/name: argocd-image-updater-config
app.kubernetes.io/part-of: argocd-image-updater
name: argocd-image-updater-config
---
apiVersion: v1
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/name: argocd-image-updater-ssh-config
app.kubernetes.io/part-of: argocd-image-updater
name: argocd-image-updater-ssh-config
---
apiVersion: v1
kind: Secret
metadata:
labels:
app.kubernetes.io/name: argocd-image-updater-secret
app.kubernetes.io/part-of: argocd-image-updater
name: argocd-image-updater-secret
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/name: argocd-image-updater
app.kubernetes.io/part-of: argocd-image-updater
name: argocd-image-updater
spec:
selector:
matchLabels:
app.kubernetes.io/name: argocd-image-updater
strategy:
type: Recreate
template:
metadata:
labels:
app.kubernetes.io/name: argocd-image-updater
spec:
containers:
- command:
- /usr/local/bin/argocd-image-updater
- run
env:
- name: APPLICATIONS_API
valueFrom:
configMapKeyRef:
key: applications_api
name: argocd-image-updater-config
optional: true
- name: ARGOCD_GRPC_WEB
valueFrom:
configMapKeyRef:
key: argocd.grpc_web
name: argocd-image-updater-config
optional: true
- name: ARGOCD_SERVER
valueFrom:
configMapKeyRef:
key: argocd.server_addr
name: argocd-image-updater-config
optional: true
- name: ARGOCD_INSECURE
valueFrom:
configMapKeyRef:
key: argocd.insecure
name: argocd-image-updater-config
optional: true
- name: ARGOCD_PLAINTEXT
valueFrom:
configMapKeyRef:
key: argocd.plaintext
name: argocd-image-updater-config
optional: true
- name: ARGOCD_TOKEN
valueFrom:
secretKeyRef:
key: argocd.token
name: argocd-image-updater-secret
optional: true
- name: IMAGE_UPDATER_LOGLEVEL
valueFrom:
configMapKeyRef:
key: log.level
name: argocd-image-updater-config
optional: true
- name: GIT_COMMIT_USER
valueFrom:
configMapKeyRef:
key: git.user
name: argocd-image-updater-config
optional: true
- name: GIT_COMMIT_EMAIL
valueFrom:
configMapKeyRef:
key: git.email
name: argocd-image-updater-config
optional: true
- name: IMAGE_UPDATER_KUBE_EVENTS
valueFrom:
configMapKeyRef:
key: kube.events
name: argocd-image-updater-config
optional: true
image: quay.io/argoprojlabs/argocd-image-updater:v0.12.0
imagePullPolicy: Always
livenessProbe:
httpGet:
path: /healthz
port: 8080
initialDelaySeconds: 3
periodSeconds: 30
name: argocd-image-updater
ports:
- containerPort: 8080
readinessProbe:
httpGet:
path: /healthz
port: 8080
initialDelaySeconds: 3
periodSeconds: 30
volumeMounts:
- mountPath: /app/config
name: image-updater-conf
- mountPath: /app/config/ssh
name: ssh-known-hosts
- mountPath: /app/.ssh
name: ssh-config
serviceAccountName: argocd-image-updater
volumes:
- configMap:
items:
- key: registries.conf
path: registries.conf
- key: git.commit-message-template
path: commit.template
name: argocd-image-updater-config
optional: true
name: image-updater-conf
- configMap:
name: argocd-ssh-known-hosts-cm
optional: true
name: ssh-known-hosts
- configMap:
name: argocd-image-updater-ssh-config
optional: true
name: ssh-config- ArgoCD 이미지 업데이터 배포
- kubectl 적용 -n argocd -fhttps://raw.githubusercontent.com/argoproj-labs/argocd-image-updater/stable/manifests/install.yaml>
ArgoCD CLI 설치
curl -sSL -o argocd-linux-amd64 <https://github.com/argoproj/argo-cd/releases/latest/download/argocd-linux-amd64>
sudo install -m 555 argocd-linux-amd64 /usr/local/bin/argocd
rm argocd-linux-amd64
ArgoCD 로그인
kubectl patch svc argocd-server -n argocd -p '{"spec": {"type": "LoadBalancer"}}'
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d; echo
argocd login localhost
로그 수준 설정
kubectl edit configmap argocd-image-updater-config -n argocd
apiVersion: v1
kind: ConfigMap
data:
# log.level can be one of trace, debug, info, warn or error
log.level: debug
로컬 계정 설정
kubectl edit configmap argocd-cm -n argocd
apiVersion: v1
kind: ConfigMap
data:
# api 접근 용도로만 사용할꺼기 때문에 apiKey 만 적어준다
accounts.image-updater: apiKey
argocd account list
계정 권한 설정
kubectl edit configmap argocd-rbac-cm -n argocd
apiVersion: v1
kind: ConfigMap
data:
policy.csv: |
p, role:image-updater, applications, get, */*, allow
p, role:image-updater, applications, update, */*, allow
g, image-updater, role:image-updater
policy.default: role.readonly
Argo CD 끝점 설정
kubectl edit configmap argocd-image-updater-config -n argocd
apiVersion: v1
data:
applications_api: argocd
argocd.grpc_web: "true"
argocd.insecure: "false"
argocd.plaintext: "false"
argocd.server_addr: <argocd 접속 주소>
kind: ConfigMap
- applications_api: argocd로 수정
- argocd.grpc_web : GRPC over HTTP/2 대신 GRPC_WEB 프로토콜을 사용할지 여부
- argocd.insecure: Argo CD API 끝점에서 유효하지 않은 TLS 인증서를 무시할지 여부
- argocd.plaintext : TLS(https) 대신 일반 텍스트 연결(http)을 사용할지 여부.
도커 허브 지정
kubectl edit configmap argocd-image-updater-config -n argocd
data:
registries.conf: |
registries:
- name: Docker Hub
prefix: docker.io
api_url: <https://registry-1.docker.io/kangbock/nginx:latest>
credentials: secret:argocd/dockerhub-secret
defaultns: library
default: true
- name: Docker Hub
prefix: docker.io
api_url: <https://hub.docker.com/repository/docker/kangbock/nginx/general>
credentials: secret:argocd/dockerhub-secret
defaultns: library
default: true
- 관로
pipeline {
agent any
environment {
GIT_URL1 = "https://github.com/kangbock/jenkins.git"
GIT_URL2 = "https://github.com/kangbock/ArgoCD.git"
}
tools {
nodejs "nodejs-tool"
}
stages {
stage('Pull1') {
steps {
git url: "${GIT_URL1}", branch: "main", poll: true, changelog: true
}
}
stage('Build1') {
steps {
sh 'docker build -t kangbock/nginx:${BUILD_NUMBER} ./nginx/'
sh 'docker build -t kangbock/nodejs:${BUILD_NUMBER} ./nodejs/'
}
}
stage('Push1') {
steps{
sh 'docker push kangbock/nginx:${BUILD_NUMBER}'
sh 'docker push kangbock/nodejs:${BUILD_NUMBER}'
}
}
stage('Pull2') {
steps {
git url: "${GIT_URL2}", branch: "main", poll: true, changelog: true
}
}
stage('Build2') {
steps {
sh "sed -i ':%s/newTag:.*/newTag:${BUILD_NUMBER}/g' ./overlays/dev/kustomization.yaml"
}
}
stage('Push2') {
steps{
withCredentials((gitUsernamePassword(credentialsId: 'dockerhub-secret'))) {
sh 'git config --global user.name "lkb"'
sh 'git config --global user.mail "[email protected]"'
sh 'git remote remove origin'
sh 'git remote add origin ${GIT_URL2}'
sh 'git add .'
sh 'git commit -m "step ${BUILD_NUMBER}"'
sh 'git push origin main'
}
}
}
stage('Finish') {
steps{
sh 'docker images -qf dangling=true | xargs -I{} docker rmi {}'
sh 'docker image prune -af'
}
}
}
}
kubectl exec -n argocd –stdin –tty 포드/argocd-image-updater-84ffbd4747-55ssl — /bin/sh
- argocd-image-updater.argoproj.io/image-list : alias=kangbock/nginx:latest
- argocd-image-updater.argoproj.io/alias.pull-secret : pullsecret:argocd/dockerhub-secret
- argocd-image-updater.argoproj.io/write-back-method: git(git 또는 argocd)
- argocd-image-updater.argoproj.io/alias.update-strategy:latest
- argocd-image-updater.argoproj.io/alias.allow-tags : Regexp :^(0-9a-f){7}$
- argocd-image-updater.argoproj.io/write-back-target: kustomization:./
kubectl 로그 포드/argocd-image-updater-8687d55bb-mxdn2 -n argocd
kubectl -n argocd-rollout 배치 재시작 argocd-image-updater
kubectl create -n argocd secret docker-registry dockerhub-secret --docker-username "kangbock" --docker-password='' [email protected]